Virtual Server Preparation
HTTP access¶
Note
loc.io - the basic domain of location.
To create HTTP access, the user needs to perform the following steps:
-
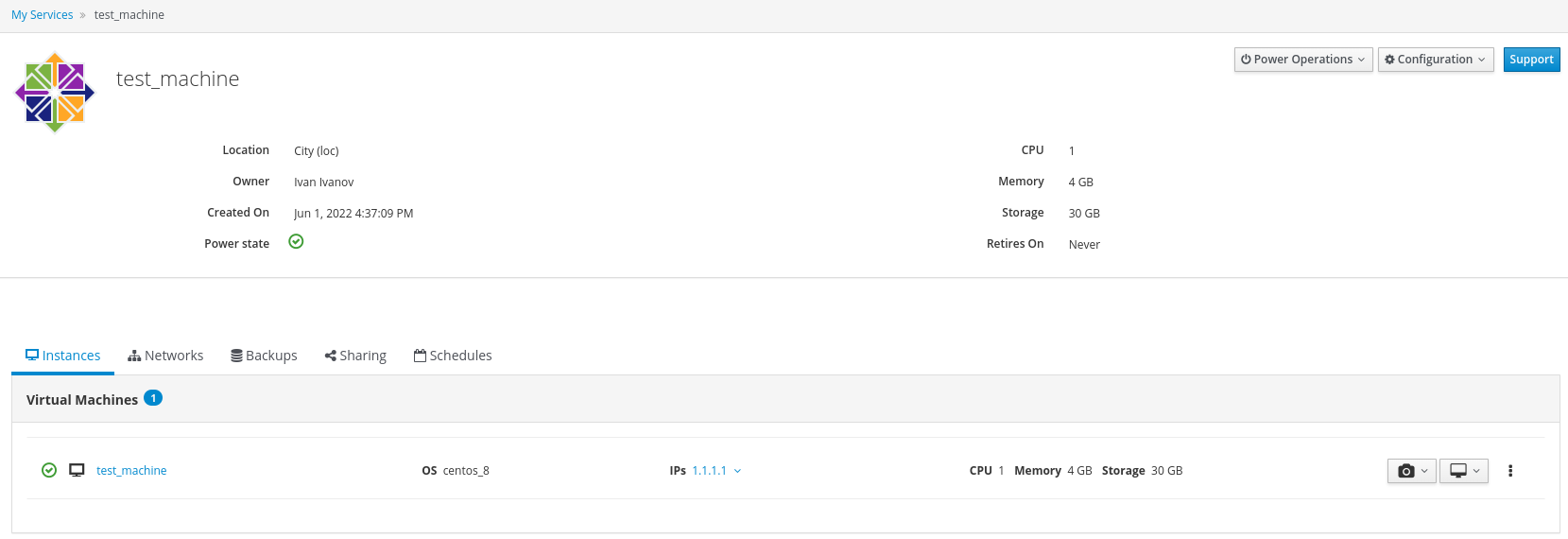
Order a service in Compute (for example, CentOS 8.3).
-
Set up VPN access in the VPN service.
-
Connect to the virtual machine, for example, via SSH (ssh root@1.1.1.1).
-
Install a web server:
- Install a web server (example: apache):
- Start the web server:
- Check if the web server is running:
Command Output Example
httpd.service - The Apache HTTP Server Loaded: loaded (/usr/lib/systemd/system/httpd.service; enabled; vendor preset: disabled) Active: active (running) since Wed 2022-05-25 10:34:11 +03; 7s ago Docs: man:httpd.service(8) Main PID: 103004 (httpd) Status: "Started, listening on: port 80" Tasks: 213 (limit: 23512) Memory: 26.4M CGroup: /system.slice/httpd.service ├─103004 /usr/sbin/httpd -DFOREGROUND ├─103005 /usr/sbin/httpd -DFOREGROUND ├─103006 /usr/sbin/httpd -DFOREGROUND ├─103007 /usr/sbin/httpd -DFOREGROUND └─103008 /usr/sbin/httpd -DFOREGROUND May 25 10:34:11 alb-demo1.pt35.cmp.loc.io systemd[1]: Starting The Apache HTTP Server... May 25 10:34:11 alb-demo1.pt35.cmp.loc.io systemd[1]: Started The Apache HTTP Server. May 25 10:34:11 alb-demo1.pt35.cmp.loc.loc.io httpd[103004]: Server configured, listening on: port 80-
Auxiliary commands for running a web server
-
Reload configuration (when changing configuration files):
- Restart the web server:
- Check web server operation:
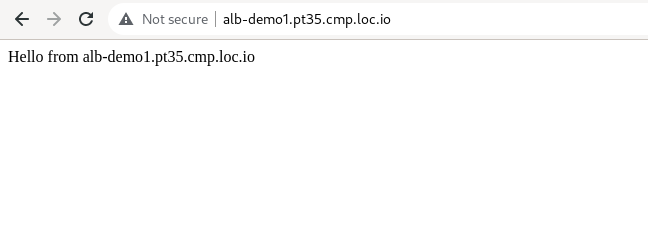
Add any text to the/var/www/html/index.htmlfile, for example: “Hello from alb-demo1.pt35.cmp.loc.icdc.io”:
!!! example
-
Setting up the system Firewall.
By default, the system Firewall blocks all HTTP and HTTPS traffic that comes from the outside on ports 80 and 443. To disable blocking, you need to add the HTTP and HTTPS services to the firewall rules. For that you need to run the commands:sudo firewall-cmd —permanent —zone=public —add-service=http sudo firewall-cmd —permanent —zone=public —add-service=https In order for the rules to apply, you need to reload the firewall configuration: sudo firewall-cmd —reloadCheck that the rules are set:
-
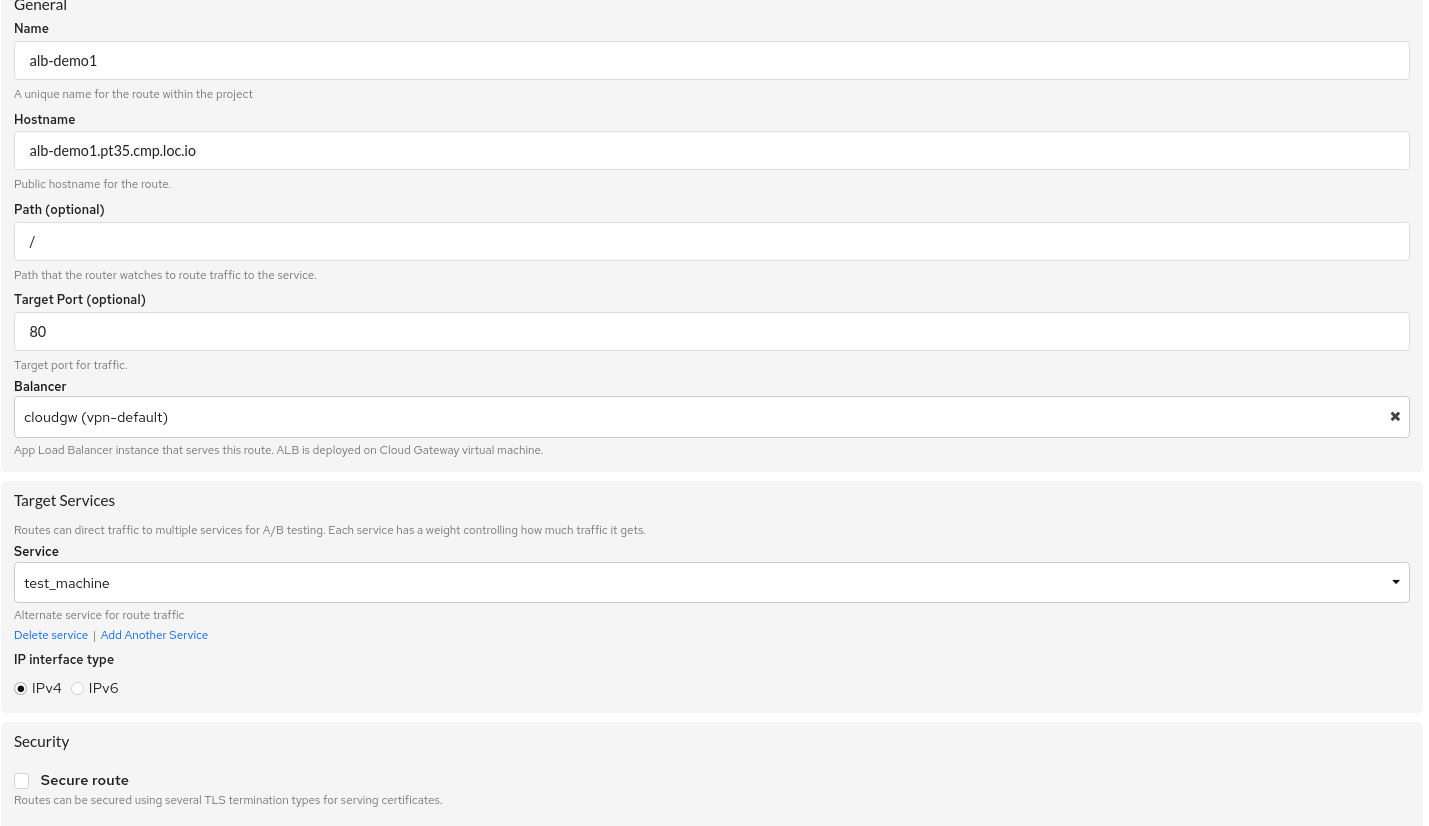
Create a public route in the Load Balancer service.
To do this, click
Create Routeand fill in the parameters (example): -
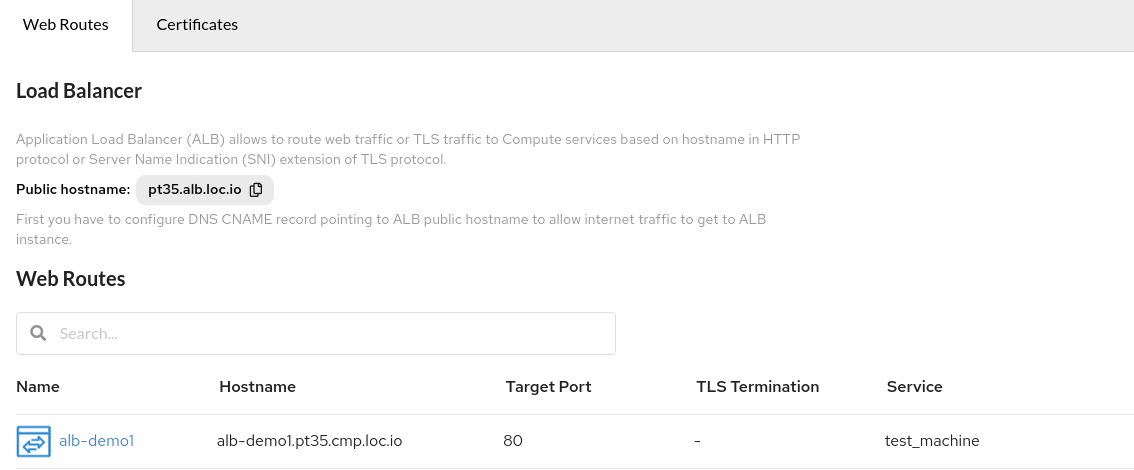
After creating a public route, for correct operation, the user needs to specify in the
DNS Domainstab that the Hostnamealb-demo1.pt35.cmp.loc.iorefers to the public host (or IP address) of the account balancer, which is indicated on the page with all web routes.
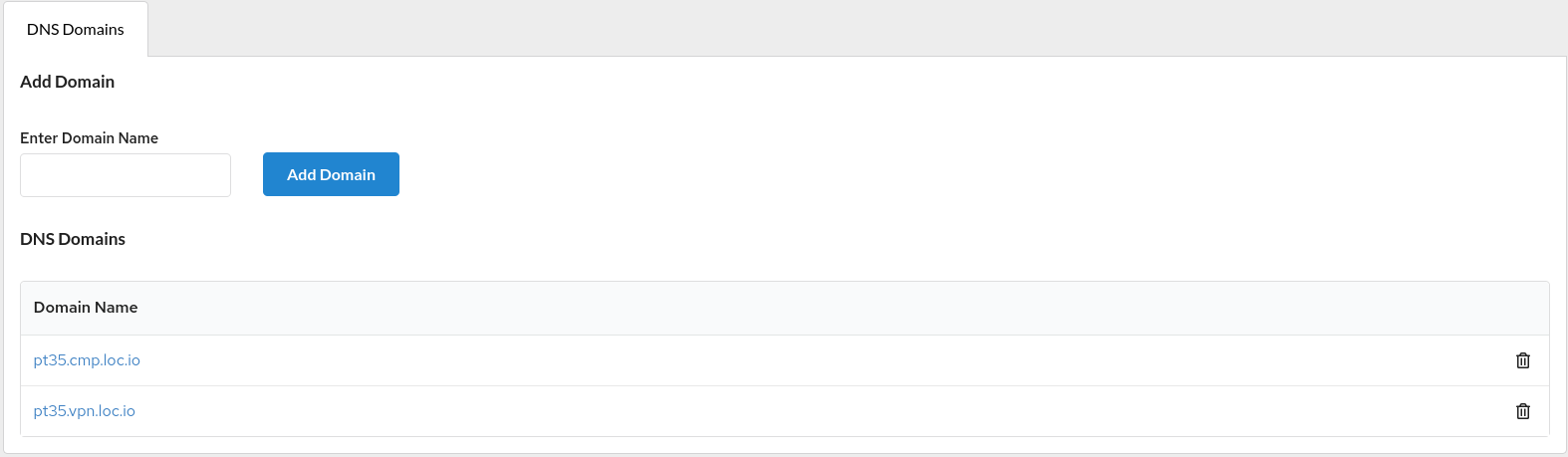
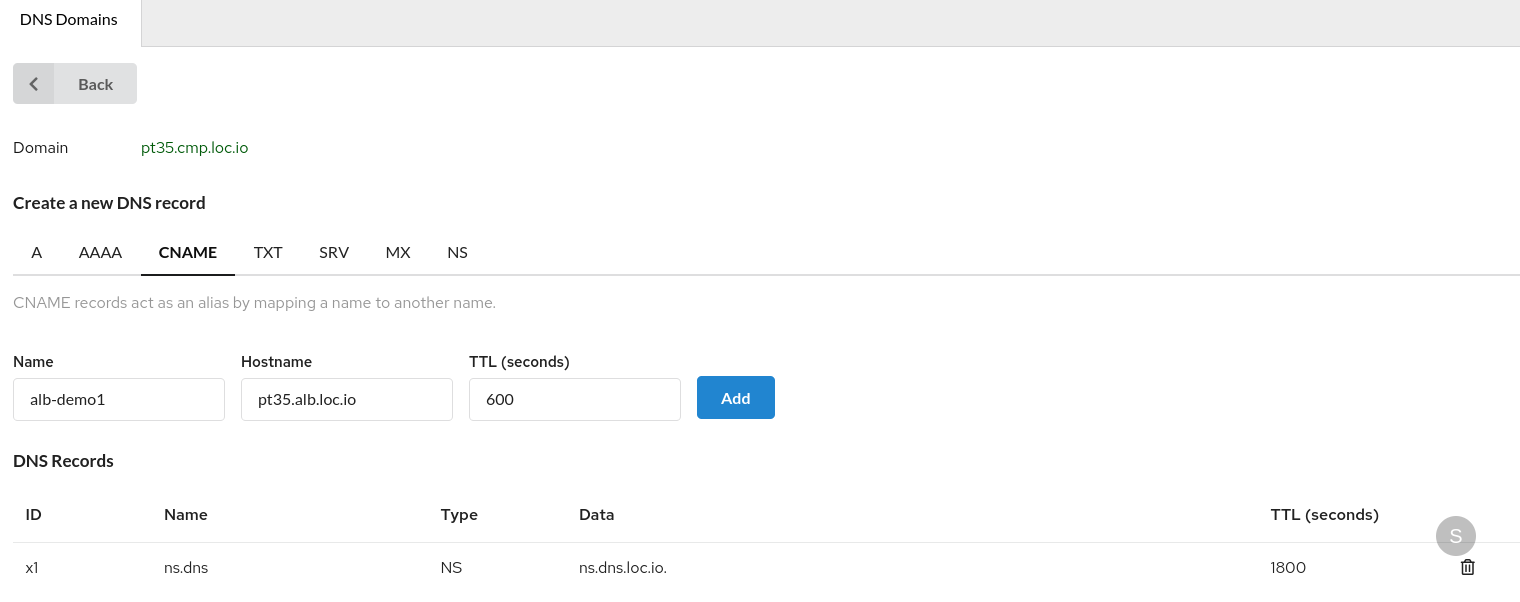
In this case, it ispt35.alb.loc.io:To add an entry to DNS, go to the
DNS domainstab.
Select the required DNS Domains (pt35.cmp.loc.io):Create a
CNAMErecord in it:Check that the public route is working. In the address bar of your browser, enter
http://alb-demo1.pt35.cmp.loc.io
HTTPS access (automatic certificate issuance)¶
Edge-termination¶
-
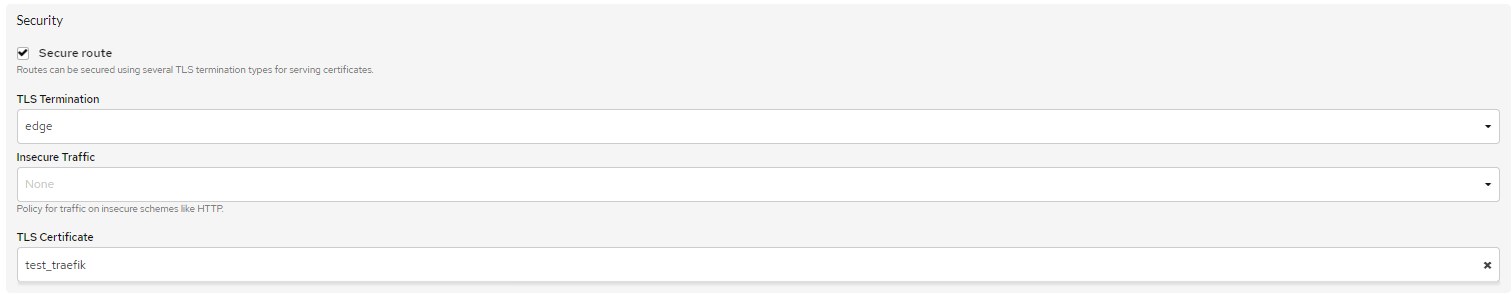
When creating a route, the user needs to check the
Secure Routecheckbox and select the type ofTLS Termination-Edge. -
Insecure Traffic:- Allow - automatic redirection from HTTP to HTTPS will not occur,
- Redirect - automatic redirect to HTTPS.
-
If the TLS certificate is not selected (
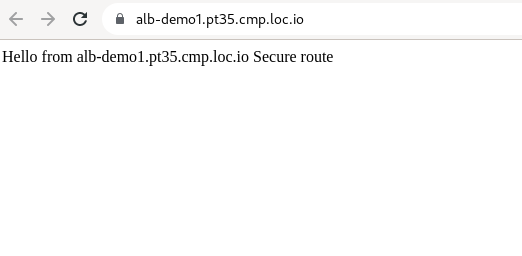
None), the LetsEncrypt certificate will be generated.Check that the public route is working.
In the address bar of your browser, enter http://alb-demo1.pt35.cmp.loc.io
Re-encrypt-termination¶
If HTTPS is used on the destination virtual server, then this option must be selected.
-
When creating such a route, the user needs to check the
Secure Routecheckbox and the type ofTLS Termination-Re-encrypt. -
Insecure Traffic:- Allow - automatic redirection from HTTP to HTTPS will not occur,
- Redirect - automatic redirect to HTTPS.
-
If the TLS certificate is not selected (
None), the LetsEncrypt certificate will be generated.
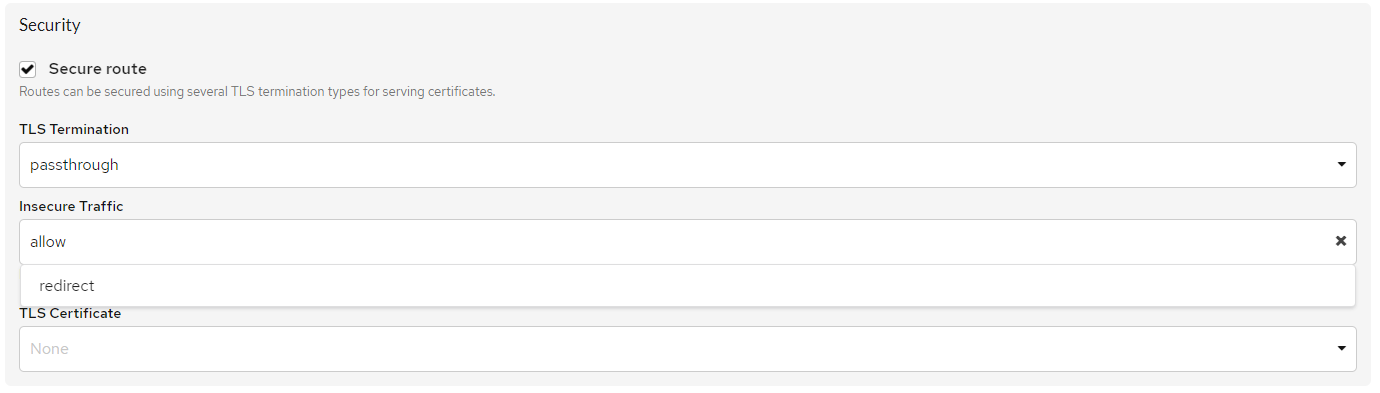
Passthrough-termination¶
-
When creating a route, the user must check the
Secure Routecheckbox and select the type ofTLS Termination-Passthrough. -
Insecure Traffic:
- Allow - automatic redirection from HTTP to HTTPS will not occur,
- Redirect - automatic redirect to HTTPS.
HTTPS access using your own certificates¶
Upload your certificate in the certificate upload dialog box.
When creating a route, you can specify the added certificate in the TLS Certificate field. Within 90 seconds, it will be added to the route.