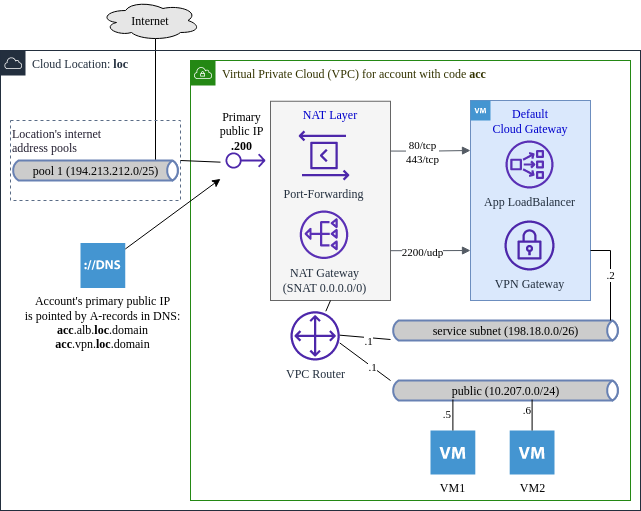
VPC resources¶
Virtual Private Cloud (VPC) is a set of dedicated cloud networks connected to a virtual router. These cloud networks are used to host Compute service virtual machines.
VPC allows you to create secure and easy-to-manage virtual networks, as well as define routes to external networks.
After registration, a new account customer gets default VPC resources:
- Virtual Router (aka
VPC Router); - Public IP configured as SNAT (for outgoing internet);
- Default route (
0.0.0.0/0) to access internet; - Base networks connected to VPC Router (usually, at least one
10.207.X.0/24, whereX- is the decimal code of location); - Service Network is also connected to VPC Router (usually,
198.18.0.0/26).
Also an account gets ALB/VPN/DNS resources:
- CloudGateway VM in the Service Network;
- Port-Forwarding for ports:
80/tcp,443/tcp,2200/udp, which send traffic to default CloudGateway; - Firewall (aka
Network Security Group), which opens ports80/tcp,443/tcpand2200/udpon CloudGateway; - Firewall NSG
Default, which opens egress (outgoing) traffic to each VM in the account; - DNS zones:
acc.cmp.LOC.icdc.io,acc.vpn.LOC.icdc.io.
Additionally, several types of direct connection to the cloud can be optionally provided by request:
- DirectConnect network connected to VPC Router, IP range configured according to customer's routing domain and can vary.
Public IP¶
Primary public IP is associated to VPC and selected randomly from shared IP pool.
Currently primary public IP address is used for 2 main purposes:
- Provides access from VMs to internet
- Access public ports of account's VMs (as well as ALB and VPN services) using
Port-Forwardrecords
Access to public IP
Currently accessing from VMs to primary public IP address is not supported. If you try to access public IP you will get "connection timeout".
To workaround this limitation use two different DNS records one used by internet clients which resolves into public IP address, another one for internal clients (e.g. VMs) which resolves in private IP address.
If you have to use only single DNS record for public and internal users, try to workaround this limitation by creating DNS zone in DNS service and redefine DNS name with private IP address. In this case internal clients will use location's DNS server as primary DNS server and will resolve it into private IP.
If you already manage DNS zone with DNS service, try to redefine DNS hostname on internal clients (internal VMs) - for example, in file /etc/hosts or HostAliases for Kubernetes.